Studio Security Overview
Introduction
This document provides clarification of questions we receive from Bluebeam Studio™ users regarding document and system security, access control, and the consequences of an infrastructure failure.
Accessing Bluebeam Studio
In order to participate in Studio Sessions and Projects, users must enter a username and password associated with your Bluebeam ID (BBID). To learn how to create a BBID, visit this article.
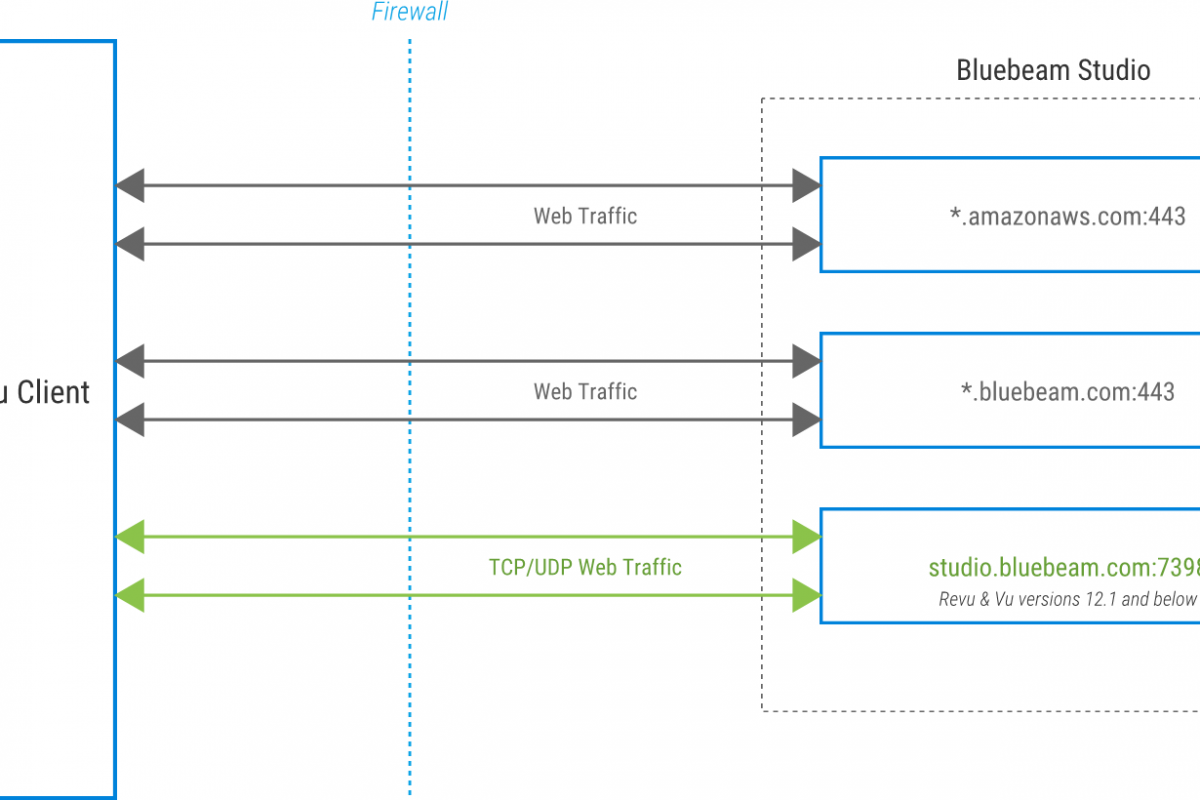
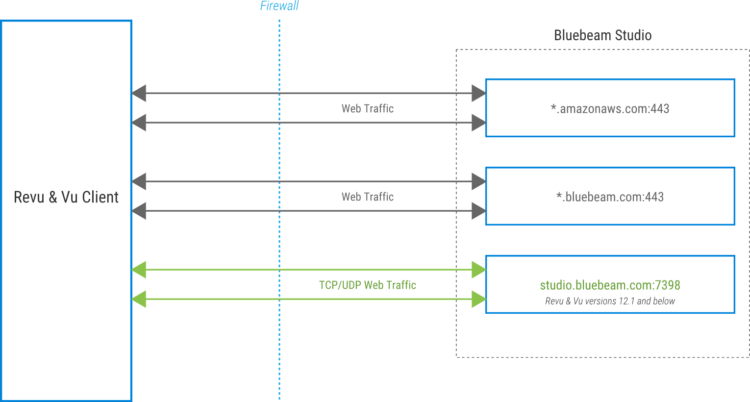
Studio server connections are initiated by Revu clients, but the system does not send inbound connection requests back to the client. Primary communication and transmission of files, markups and other rich data uses the HTTPS protocol, while encryption and authentication uses the Transport Layer Security (TLS) protocol.
Firewall Requirements
Below are the domains that are used by Studio services environments. If you are only accessing a specific Studio environment, you only need to allowlist the domains specific for that environment, along with the required global services.
Global Services:
*.amazonaws.com:443
*.gds.bluebeam.com:443
*.login.okta.com:443
US Environment:
*.bluebeam.com:443
UK Environment:
*.bluebeamstudio.co.uk:443
AUS Environment:
*.bluebeamstudio.com.au:443
DE Environment:
*.bluebeamstudio.de:443
SE Environment:
*.bluebeamstudio.se:443
Studio-Related Email Domains
We use the following domains to communicate with end-users for support, licensing and Studio-related information. White-listing these domains may be necessary to ensure successful email transmission:
US Environment:
@bluebeam.com
@bluebeamops.com
@bluebeam-support.com
UK Environment:
@bluebeamstudio.co.uk
AUS Environment:
@bluebeamstudio.com.au
DE Environment:
@bluebeamstudio.de
SE Environment:
@bluebeamstudio.se
End-User Authentication & Access Control
The following protocols have been implemented for secure end-user authentication and access control:
Certificate Requirements
Connections to Studio environments, such as studio.bluebeam.com, are encrypted using a Public Key Infrastructure-based (PKI) SSL certificate, issued by Amazon Web Services Certificate Authority (AWS CA).
The certificate may be viewed by going to https://studio.bluebeam.com and clicking the padlock icon, located near the beginning of the URL in the address bar.
Password Requirements & Storage
All passwords must be between 8 and 32 characters, with at least one uppercase letter, one lowercase letter, one number and one special character, such as !@#$%^&*.
Password are hashed prior to storage, using a one-way strong hash algorithm with salt.
In addition, an algorithm locks accounts for a 5 minute interval after 5 successive login attempts using an incorrect password. Login failures are logged, and our operations team is alerted if the quantity rises above a preset level.
Data and System Security
The measures described below have been implemented to address data and system security concerns.
Infrastructure and Data Storage
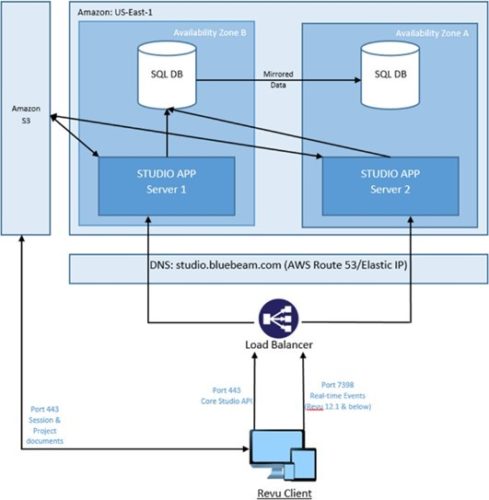
Bluebeam Studio is hosted on Amazon Elastic Compute Cloud (EC2) managed by Amazon Web Services (AWS).
The Studio infrastructure is comprised of application servers which serve Revu clients on Windows, macOS, and iOS, as well as a backend processing system and a data tier.
User data, Project and Session metadata, and Session markups are stored on SQL servers. Actual Project and Session documents reside on Amazon Simple Storage Service (Amazon S3) servers.
Bluebeam Studio has multiple isolated environments for data residency concerns located in the United States, the United Kingdom, Germany, Sweden, and Australia. The Database infrastructure and S3 buckets containing customer data are not shared between any environments. All Bluebeam Studio environments can be accessed from anywhere in the world.
SLA’s for Amazon EC2 and Amazon S3 can be found in following locations:
Data Protection
In addition to encryption of all SQL server backups and developer hard drives, all documents are automatically encrypted when uploaded to a Studio Session or Project using Revu 2015 and above, as described below.
Encryption
Encryption is done by using an AWS Key Management Service (KMS) key ID.
All data is encrypted at-rest (AES-256 encryption) and in-transit. Data transfer is encrypted in transit via TLS1.2* between the Revu client and Amazon S3. In the server environment, files are encrypted in Amazon’s S3 service. SQL database backups are stored on encrypted volumes.
System security
We’ve ensured that all environments perform in the same manner and are subjected to the same network policies and restrictions by building them with a validated and tested “template.” Once deployed, the following steps and policies are in place to provide additional security and consistency across the infrastructure:
Controlled Administrator Access
Only a select group of engineers have administrative rights within the Bluebeam Studio infrastructure, and management console access is controlled via Multi-Factor Authentication (MFA).
Change Control
All system changes and enhancements are documented and must undergo testing and approval by our DevOps and Security teams, before implementation in the production environment.
Logging
Application and system security logs are retained for a minimum of 30 days. Only DevOps engineers have access to these logs. Developer access to logs for troubleshooting must be approved by security personnel.
Vulnerability Assessment and Remediation
We’ve implemented a comprehensive vulnerability assessment and remediation process to address any security issues that may arise. These measures include antivirus protection on all servers, proactive system patching policy, and file integrity monitoring (which detects unauthorized changes to the systems).
Applications with a web component are scanned prior to and after deployment to the production environment.
All production systems are scanned for infrastructure vulnerabilities on a recurring basis and are patched accordingly.
Inventory of Authorized Assets
All production asset additions and modifications are restricted to the DevOps team and follows Change Control procedures. The DevOps team leverages AWS tools to maintain asset inventory.
Infrastructure & System Monitoring
To ensure a steady state of operations, a comprehensive monitoring and alert system is in place for the following:
- Server infrastructure: CPU, memory, disk space, and uptime.
- Applications: errors, performance degradation, and uptime.
- Network Performance: usage and bandwidth, server response time, throughput, and web requests.
System Maintenance
Regular maintenance tasks and emergency maintenance is performed in accordance with our established Change Control process.
Disaster Recovery (DR)
Bluebeam Studio DR strategy is built upon leveraging multiple AWS Availability Zones. This strategy is focused on having a highly available and distributed system to minimize risk associated with disruptions and disasters.
To handle the unfortunate event of an infrastructure failure, we’ve put the following contingencies in place:
Infrastructure Redundancy
There is full redundancy for all Studio application servers. If a primary server fails, all traffic will automatically be switched to a secondary server.
Application servers run in a cluster behind a load balancer. Studio SQL Database uses “AlwaysOn” to provide HA. DNS redundancy is provided by AWS Route53.
Additionally, Bluebeam Studio infrastructure is deployed across multiple AZs in a Multi-AZ architecture within the AWS Region.
Backup Protocol
Full backups of the SQL Databases are performed on a daily basis. The backup files are stored away from production servers, and their integrity is regularly inspected.
PDF files are stored in AWS S3, which provides highly durable storage and file versioning.
SOC2
SOC2 Compliance
The Bluebeam System and Organization Controls (SOC) Report is an independent third-party examination report that demonstrates how Bluebeam achieves key compliance controls and objectives. Bluebeam undergoes an annual SOC 2 audit performed by an external and independent third-party assessor annually to verify the implementation and effectiveness of our security controls. Our report covers the SOC 2 Trust Services Criteria of Security and Availability.
If you would like to request a copy of the report, please contact your Bluebeam representative for more information. If you do not have a Bluebeam representative, contact us for further assistance.
Bluebeam, Revu, and Bluebeam Studio are trademarks or registered trademarks of Bluebeam, Inc. Microsoft, SharePoint, and Windows are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.
AutoCAD is a registered trademark of Autodesk in the United States and/or other countries.
© 2024 Bluebeam, Inc. All Rights Reserved.
All other trademarks or registered trademarks are the property of their respective owners.
How-To
Revu 2017 & Below
Revu 2018
Revu 2019
Revu 20
Revu 21
Studio